|
Ransomware Removal

UK Technical Support
Ransomware is a form of Malware (Malicious software) which is become more and more common.
Ransomware typically attacks the users files and often encrypts them (so that they are unreadable). The user is often presented with a demand for money - ransomware is a form of extortion where the users files are held to ransom.
There are many types of ransomware, but the most prevalent form at this time (January 2016) is known as cryptolocker Ransomware.
This is actually a small Trojan Virus which is typically downloaded and installed when the user clicks on a "wrong link" online, or opens an infected email, or clicks on a link within a phishing email.
Cryptolocker Ransomware typically attacks personal files and encrypts photographs, word documents, PDF files and other documents.
The user is then presented with a message which demands payment for decrypting the documents.
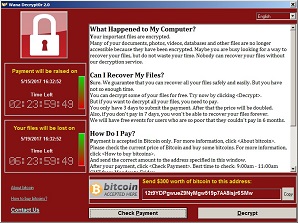
Sample Police eCrime Scam 1
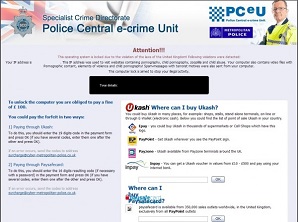
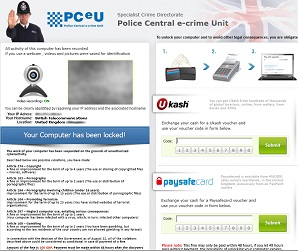
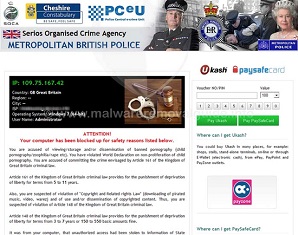
In many cases, the ransomware pretends to be a message from the police (typically Police eCrime Unit) or Microsoft and says that the user is using unlicensed software, the files have been encrypted and a payment is demanded for a key (code) which must be entered to release the users files.
Sample Police eCrime Scam 2
Sample Police eCrime Scam 3
In other cases the criminals who run this scam simply demand payment to decrypt the files.
We have tools to decrypt approximately 75000 versions of cryptolocker ransomware, but we cannot crack every cryptolocker key (cryptolocker code) because new codes are being constantly generated (this is an "arms race").
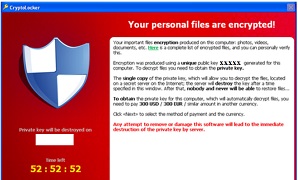
Sample Cryptolocker Screen 1
Additionally; many versions of ransomware impose a time limit to try and stop companies such as us from helping the victim. This time limit often means that files will be deleted after a certain time or if the power is turned off.
In this case the solution is to note the time of infection, disconnect internet access and turn the computer off by unplugging it (if a laptop - remove the battery and then unplug it). Under no circumstances should you turn off the computer via the power off switch in the Start section or by keeping the power button pressed for 6-8 seconds. This is to ensure that the ransomware does not have time to delete the users files.
When the computer is restarted, the engineer can go to the Bios (before loading Windows) and change the time so that it will not have reached the limit.
The engineer can remove the hard drive, connect it to a dedicated system running the best antivirus and anti spyware software which is not connected to the internet or a network and which has had the time rolled back. Remove the ransomware, copy the files to another hard disk drive or DVD etc and attempt to decrypt the files (unlock the documents).
If the files cannot be decrypted (unlocked) and if the user has no backup of the documents, then the only solution is to lose the files or pay the criminals.
If the user has a backup; these should be checked and also backed up. Kill the ransomware on the computer hard drive and copy the files from the backup.
Anti Ransomware Software
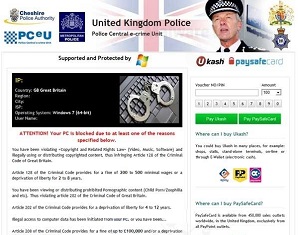
Sample Police eCrime Scam 4
There are many different brands of anti virus and anti malware software, but most cannot successfully find or remove ransomware (such as Cryptolocker Ransomware).
Free anti Virus software (including Microsoft Essentials anti virus software) tends to be far less effective than paid for anti virus software. Eg; on new years day 2016, we removed Cryptolocker ransomware from a PC which had the paid for version of AVG installed. In this particular case, AVG found nothing. Kaspersky found three trojan viruses and Malwarebytes found 28 malware infections. We believe that using free or non premier anti virus software or anti malware software is often a false economy which can have catastrophic consequences.
Additionally, all security updates should be installed (these should be automatically applied during Windows Updates), but the best form of protection against ransomware is to regularily backup important files (documents, photos etc).
Statistics
Source; Malwarebytes
48%of companies were found to have suffered a ransomware attack. Of these; 58% paid the ransom, however; in many cases, the encrypted data was not released and in many others, the data was compromised and - or modified to enable re-encryption at the discretion of the attackers.
May 2017 Ransomware Attack
Please Note
We can now confirm that following the May 2017 UK Cyber Attack (May 2017 Ransomware Attack), no current A&A Computer Repair clients or A&A Computer Repair customers were affected.
Please Click Above to View
Wannacry Ransomware was so named because it encrypted personal files and used the file extension .wncry
At the time of writing, the media are claiming that the attack originated in N Korea. However, we believe that it is far more likely to have originated in Eastern Europe.
However, we completely agree that such ransomware attacks will re-occur and that the actual ransomware software will evolve and improve (we are in an "arms race with these criminals").
Basic Anti Ransomware Advice
Please Click Below to View CBS News Report
Hacking - Ransomware Security Report
Ransomware Removal
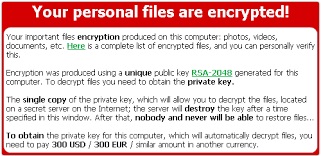
Sample Cryptolocker Screen 2
The first course of action is always to delete any ransomware infections.
We typically remove the computer hard drive and connect to a dedicated machine which is running the best anti virus and anti malware software and we perform a full scan - ransomware removal.
We then backup the customers files (which will also have been disinfected) and rescan them.
During this process, we routinely service the computer (clean connections, remove dusts and fluff from the fan and air intakes, exhaust ports etc.
In most cases, the ransomware issue will now be resolved. If all signs of the ransomware are removed and the customer is happy for us to do so; we will test for and resolve internet issues (eg; Google Chrome, Internet Explorer or Firefox could be configured to auto access an infected website - to re-infect the computer) and we perform Windows updates.
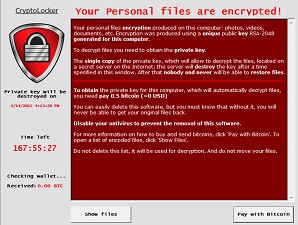
PClock2 Ransomware
If we perform a full reinstall; we delete all existing hard drive partitions (to completely erase the hard drive) and then perform a full Windows reinstallation. This returns the computer software to "as new" - "out of the box" state and guarantees that the computer is virus free and ransomware free. We then transfer the customers files back to the computer and usually install quality anti virus software and anti malware software.
Finally we download and install Windows updates (please note; this can take 24 hours).
We also retain backup copies of the customers files for at least 30 days.
However; the customer will need to reinstall any programs which he or she installed, but in most cases the computer will be significantly quicker.


No Fix - No Fee
Finding and removing computer viruses since 1987
To date; we have a 100% record.
Average Turnaround time - 24hrs